You can find the SAINTCON 2014 Hackers Challenge Introduction here.
And this is all the files referenced below: SAINTCON_2014_Hackers_Challenge_PT.zip
The challenges referenced below can be found here:
Contents
PT100 – Some Pain
Puzzle:
Answer the questions and you may move on... Hint: - Space is a valid password character. Files: Fixed Version PT100-fixed.zip
Solution:
———————————————–
The answer to this question will open the next file:
This Microsoft application had a “Flight Simulator” embedded in it
(The Password Will Be In ALL LOWER CASE)
microsoft excel 97
———————————————–
The answer to this question will open the next file:
Largely regarded as the first “Clone” computer, this computer was made famous for starting “Global Thermal Nuclear War”.
(The Password Will Be In ALL LOWER CASE)
imsai 8080
———————————————–
The answer to this question will open the next file:
This Atari 2600 game contained the first documented electronic “easter egg”
(The Password Will Be In ALL LOWER CASE)
adventure
———————————————–
The answer to this question will open the next file:
This Extended character known as Dagger shares it’s hex value with this Instruction Set Architecture
(The Password Will Be In ALL LOWER CASE)
x86
———————————————–
The answer to this question will open the next file:
A Flight Simulator, a Pinball Game, and a Magic 8 Ball, were easter eggs in this “Suite” of software
(The Password Will Be In ALL LOWER CASE)
microsoft office 97
———————————————–
The answer to this question will open the next file:
This RFC makes private a /8 /12 and a /16
(The Password Will Be In ALL LOWER CASE)
rfc 1918
———————————————–
The answer to this question will open the next file:
This floating point number defines the IEEE standard for Ethernet
(The Password Will Be In ALL LOWER CASE)
802.3
———————————————–
The answer to this question will open the next file:
Ethereal, but for today
(The Password Will Be In ALL LOWER CASE)
wireshark
———————————————–
The answer to this question will open the next file:
Only way to win is not to play
(The Password Will Be In ALL LOWER CASE)
tic-tac-toe
———————————————–
The answer to this question will open the next file:
This TCP flag tells the sender “I got your message”!
(The Password Will Be In ALL LOWER CASE)
ack
———————————————–
The answer to this question will open the next file:
whois 172.16.2.4, tell 172.16.2.5
(The Password Will Be In ALL LOWER CASE)
arp
———————————————–
The answer to this question will open the next file:
This is the “secure” meaning of ACL
(The Password Will Be In ALL LOWER CASE)
access control list
———————————————–
The answer to this question will open the next file:
Brings color to your console
(The Password Will Be In ALL LOWER CASE)
ansi
———————————————–
The answer to this question will open the next file:
Replaced DES as a US Standard
(The Password Will Be In ALL LOWER CASE)
aes
———————————————–
The answer to this question will open the next file:
802.11 is the IEEE standard for this technology
(The Password Will Be In ALL LOWER CASE)
wireless
———————————————–
The answer to this question will open the next file:
This floating point number defines the IEEE standard for Ethernet
(The Password Will Be In ALL LOWER CASE)
802.3
———————————————–
The answer to this question will open the next file:
This RFC defines the use of the 172.16/12 as Private Addresses
(The Password Will Be In ALL LOWER CASE)
rfc1918
———————————————–
The answer to this question will open the next file:
This protocol is defined by RFC2616
(The Password Will Be In ALL LOWER CASE)
http
———————————————–
The answer to this question will open the next file:
Codename for Windows 98
(The Password Will Be In ALL LOWER CASE)
memphis
———————————————–
Key: memphis
PT200 – Some More Pain
Puzzle:
Geocache to your hearts content.. Hint -Look for Photos! -Use Google Earth -Second Password is: self parking -Use Panoramio Photos Zip File PT200.zip If you got this far, and found a bad zip file... puzzle_0048.zip
Solution:
I don’t have my notes on these right now, but here is a start:
Pull up each coordinate in Google earth, and view available photos or place names:
————————————————-
Digital Geocache, find the keyword at the following location to open the next file::
37° 33′ 6.66″ N 115° 37′ 35.00″ W
(The Password Will Be In ALL LOWER CASE)
little aleinn
————————————————-
Digital Geocache, find the keyword at the following location to open the next file::
37° 14′ 36.52″ N 115° 48′ 41.16″ W
(The Password Will Be In ALL LOWER CASE)
self parking
————————————————-
Digital Geocache, find the keyword at the following location to open the next file::
43° 5′ 12.20″ N 79° 3′ 49.88″ W
(The Password Will Be In ALL LOWER CASE)
hard rock cafe
————————————————-
Digital Geocache, find the keyword at the following location to open the next file::
34° 6′ 6.71″ N 118° 20′ 23.20″ W
(The Password Will Be In ALL LOWER CASE)
Key:
PT300 – Gigantus
Puzzle:
Initial Clue: Use p7zip (7z) or LZMA Included Files: Gigantus.7z Hope you have a big Hard Drive! Files: 7-Zip File PT300.7z
Solution:
Well, you can’t really extract this file to disk, it will be several terabytes.
But if you want to try, I have a suggested method for that too.
LEARN MORE:
http://en.wikipedia.org/wiki/Null_character
http://en.wikipedia.org/wiki/Sparse_file
http://sc.tamu.edu/help/general/unix/redirection.html
https://developer.apple.com/library/mac/documentation/Darwin/Reference/ManPages/man1/tee.1.html
Method 1: Create a sparse disk image, extract the file to it. As the NULL bytes get’s extracted it won’t be written to disk.
Use SED, AWK, GREP, or any other tool to remove the null bytes from the extracted file.
BEST WAY:
So let’s just play in RAM.
On windows PS C:\Program Files\7-Zip> .\7z e c:\Downloads\PT300.7z -so 2> c:\Dwonloads\garbage.txt | foreach { $_ -replace "null","" } This is REALLY slow, but it works. (takes lots of RAM, powershell doesn’t hanle the -replace efficiently it seems)
Or OS X 7z e PT300.7z -so | tee you’ll start to see letters appear. (Still takes a long time)
Joshs-MacBook-Pro:FIles zevlag$ 7z e PT300.7z -so | tee 7-Zip [64] 9.20 Copyright (c) 1999-2010 Igor Pavlov 2010-11-18 p7zip Version 9.20 (locale=utf8,Utf16=on,HugeFiles=on,4 CPUs) Processing archive: PT300.7z Extracting PT300GIGANTUS -- LUCY!... You got a lot'a processing to do... A B i l l i o n Z e r o s W O W Is your computer tired yet? Everything is Ok Size: 322122547317 Compressed: 45439340
Key: ABillionZerosWOW
PT400 – ZippiDeeOhhNoo
Puzzle:
Initial Clue: The password for the zip file is included in the .pass file
Included Files: ZippiDeeOhhNoo.zip
ZippiDeeOhhNoo.pass
The Key is in the ZIP file. Buy you need to figure out how to get it.
And you need to automate it, cuz there are 4092 iterations.
Files:
ZIP File PT400.zip
Solution:
Will after playing with this one for awhile, getting a list of file names in the zip, etc. It appears we are missing a part. I’m guessing that ZippiDeeOhhNoo.zip got renamed to PT400.zip, and ZippiDeeOhhNoo.pass was never uploaded.
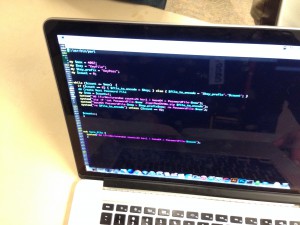
Calling bull on the puzzle, I got a screen shot of the code that generated it.
#!/usr/bin/perl
my $max = 4092;
my $key = "KeyFile";
my $key_prefix = "KeyPass";
my $count = 0;
while ($count <= $max) {
if ($count == 0) {$file_to_encode = $key; } else {$file_to_encode = "$key_prefix"."$count";}
## Create Next Password File
my $new = $count+1;
system("dd if=/dev/urandom count=24 bs=1 | base64 > PasswordFile-$new");
system("zip -P `cat PasswordFile-$new` ZippiDeeOhhNo.zip $file_to_encode");
system("base64 PasswordFile-$new > $key_prefix$new; rm PasswordFile-$new");
system("rm $file_to_encode") unless ($count == 0);
$count++;
}
sub turn_file {
system("dd if=/dev/urandom count=24 bs=1 | base64 > PasswordFile-$count");
}
Essentially:
- KeyFile is in ZippiDeeOhhNo with password of 24bytes of random base64
- KeyPass1 contains base64 of Password to KeyFile
- KeyPass2 contains base64 of Password to KeyPass1
- KeyPass3 contains base64 of Password to KeyPass2
- ….
- KeyPass4092 contains base64 of Password to KeyPass4091
So I’d expect the promised ZippiDeeOhhNoo.pass to contain the password to KeyPass4092.
Then I’d write a script to handle the iterations.
Key: